I was recently involved in a project that required secure FTP connectivity between my organization and a partner organization. We continue to leverage /n Software’s SFTP adapter as we are still running BizTalk 2009 in production and we also find that our partners tend to leverage Secure FTP using SSH (SFTP) as opposed to FTP over SSL (FTPS). BizTalk 2010 now includes an FTP adapter that supports SSL so we are likely to continue to use the /n Software adapter based upon SSH requirements even once we upgrade to BizTalk 2010.
I am very far from being a Security/Certificate expert so I did learn a few things being involved in this project. Hopefully if you have Secure FTP requirements that you will find this post helpful.
Generating Public and Private Keys
In my scenario, our trading partner required us to provide them with our Public key. They wanted us to generate Private and Public keys. They would then take our public key and install it in their SFTP server. To generate these keys I simply used GlobalScape’s CuteFTP 8.3 Professional.
Note: Your mileage may vary here. There are some requirements that were enforced by our Trading partner including the Key type and the number of bits required for encryption.
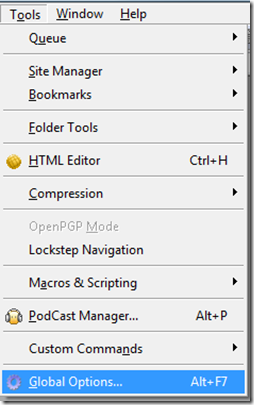
1. Click on Tools -> Global Options
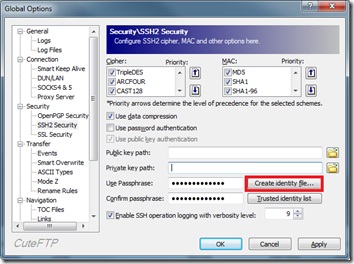
2. Click on Create identity file
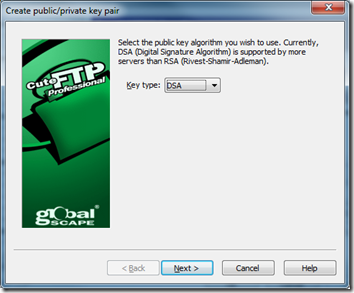
3. Use DSA
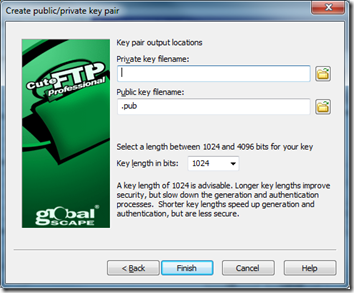
4. Provide a Passphrase
5. Enter a location for files to be generated and ensure the key length is set to 1024
Configuring BizTalk Receive Location
Since the Receive Location configuration is a little lengthy I am going to break it down into the various sections.
SFTP
Pretty basic settings here dealing with when we want to Delete, what file masks we want to look for and the folder on the remote SFTP server that we want to navigate to once we have successfully established connectivity.
SSH
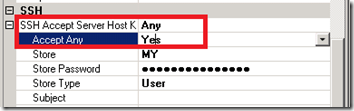
The first area to focus on in the SSH section is the SSH Accept Server Host Key. When you set the Accept Any to Yes the SSH Accept Server Host Key property will revert to Any. I equate this action with when you try to connect to an SFTP server using a client like CuteFTP. You will get prompted with a dialog asking if you would like to accept the public key being pushed from the SFTP server. The way I understand how this works is that this public key will get validated against your private key. Should everything match up you should be able to establish a connection.
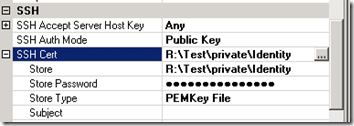
The next property to focus on is the SSH AuthMode. We want to set this value to be Public Key. There are a few different options when it comes to setting the Authentication mode. One includes setting a password but for this particular partner they wanted to use Public Key authentication. When we set this value we then need to provide the location of our private key which happens to be called Identity (without a file extension).
To provide our Private key we need to click on the ellipse button.
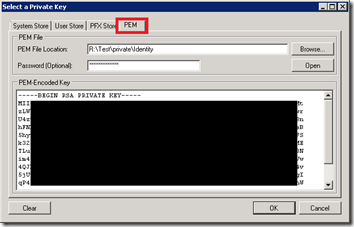
We will now be prompted with a dialog that allows us to select our Private key from a variety of sources. In my scenario I wanted to select my key from the file system. In order to do so I needed to select the PEM tab and then browse to my key. Since I have enabled my key to use a password I need to provide a password and then I can click the Open button. Once I did this my private key would appear in the TextArea box and I can click Ok.
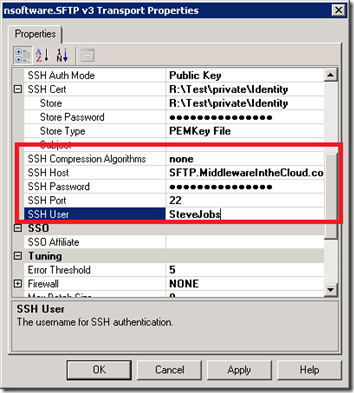
The rest of the configuration deals with some connectivity details including the name of the FICTICOUS Host and a SSH User (a tribute to Steve Jobs who has recently stepped down from being Apple’s CEO) . The SSH Port is using the default port of 22 and even though it appears as if I have provided a password that is the default mask provided by the adapter.
Conclusion
So as much as people love to talk about the cloud these days and using the Service Bus and WCF bindings, the bottom line is that companies continue to rely upon “legacy” technologies such as SFTP. In my scenario, this trading partner is a very large institution so it is not as if they are a little “Mom and Pop” shop.


No comments:
Post a Comment